I am a little bit late but Happy New Year 🙂
In the beginning of the year I decided to hack one company, let’s call it XXX as I can’t give the real name. The company is running VDP program and offers only letters of appreciacion. So I wanted to get one. I started my recon by google dorking with these dorks:
site: *.XXX ext:jsp
site:*.XXX ext:php
site:*.XXX ext:asp
I found the JSP site, looking pretty legacy, which allowed some data searching. So I ran the BURP and started playing with the site. I looked through the requests one by one but found nothing pretty interesting. So I started testing parameters for XSS, html injection but found nothing. I also tried array-based injection – instead of value I put [] as an array, it often leads to unexpected results, but nothing. I also tried adding ‘ to the end of parameters, hoping for SQL error or at least error 500 which could indicate blind SQL injection but nothing. One mistake I made back then was I omitted some parameteres and focused only on the one getting the user input value directly, not the one that were kind of control parameters adding by the app itself.
I was about to give up but somehow I put ‘ in the end of the control parameter. Suddenly, in the response I saw an SQL error… what? Good old SQL injection just like that? Yes that was it. This is heavily redacted request:
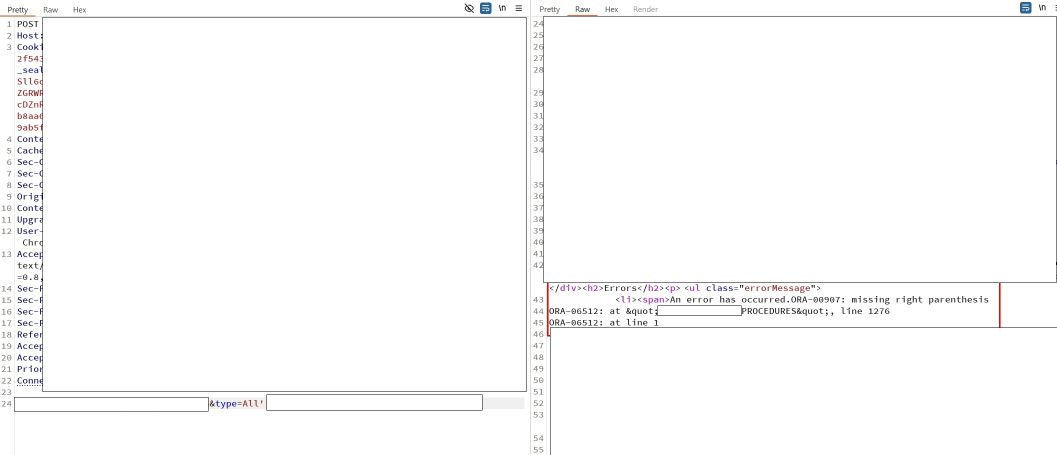
Ok, I’ve got the SQL injection, but what now. To prove the impact I had to extract some real data such as username, database name or tables name. The error points to Oracle database which fortunately I am pretty familiar with as the developer but not from the SQL injection point of view :). At first I figured out I can post only this one parameter (type) to throw the error. The error says it is procedure, so we can assume the sql is something like:
begin some_procedure(param1,param2,type); end;
that’s why I tried to close the query and see what happened:
type=All’); select 1 from dual; end;–
but another error has happend. I was trying some more payloads to end the query and begin another one, always ending up with some errors. I took a break.
Several hours later I came back with the fresh mind and new idea – what if I concatenate the value of type parameter with something else , so the injection would be:
type=x’||’abc’)–
and guess what? It worked , there was no error and I got no data , means that’s the right way of exploiting that. Now I had to check if I can run my own queries. I tried this:
type=x’||(select ‘abc’ from dual))–
and I got some strage syntax error. I figured out this might be due to the space signs so I recall the old trick replacing them with sql comments , so the we got this payload now:
type=x’||(select/**/’abc’/**/from dual))–
This worked perfectly. Again – success – no error and no data. But If a get no data in response how can I retrieve anything? The answer is special oracle function that returns the data inside of the error message. After some googling I found the perfect candidate for this:
ctxsys.drithsx.sn(1,(sql query to execute))
And to be honest, I don’t know what this function is doing, but this query returned the username (starting with N in this picture) as the part of the error message:
type=x’||(ctxsys.drithsx.sn(1,(select/**/user/**/from/**/dual))))–
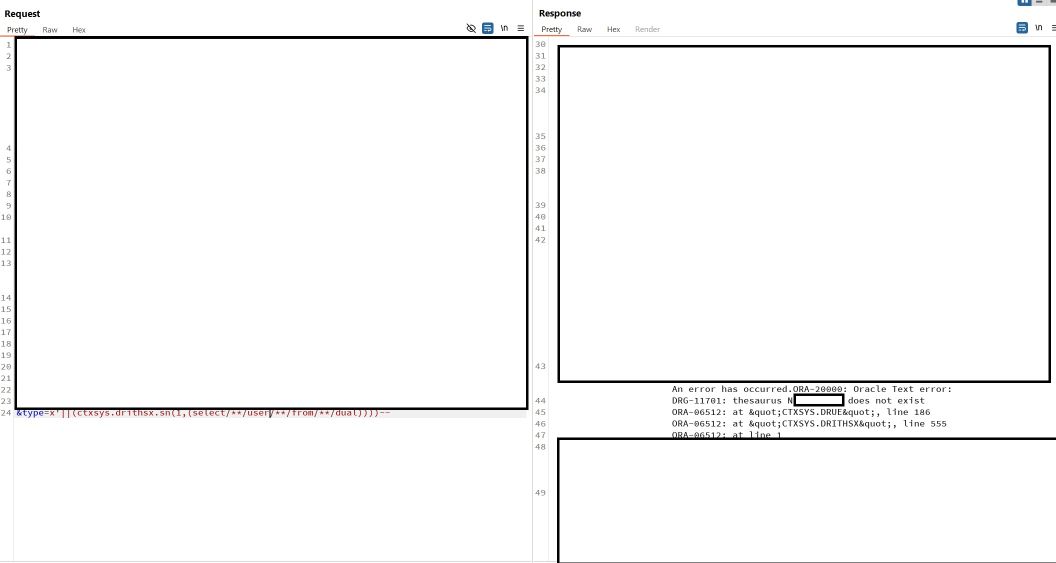
I also extracted database name with the following payload:
type=x’||(ctxsys.drithsx.sn(1,(select/**/ora_database_name/**/from/**/dual))))–
Finally I sent the report and got P1 two days later.
Reward: letter of recognition
See you next bug
