Hello folks
This time I want to tell you the story how I gained access to some admin functionalities and leaked some sensitive info using FUFF, Burp, my eyes, and brain :).
Fuzzing
Let’s call the target “redacted.com”. I started fuzzing the target with FUFF and found an /admin endpoint
https://redacted.com/app/admin
which displayed: “Sorry you’re not authorized to access the page” when entering the site. I moved on to testing other parts of an application. Later, I read Sam Curry’s article on Starbucks hacking by attacking secondary contexts :
https://samcurry.net/hacking-starbucks
I recommend reading it. I entered this site again and logged all the requests. But nothing was interesting besides the endpoint which gave me 403 response in burp. I tried playing with this endpoint as in the the article, but I quickly realized this is not the case. However, if I appended anything after the /admin/ such as:
https://redacted.com/app/admin/xxx
I’ve got 404 response, so… BINGO. It should be 403, isn’t it?.
More fuzzing
I started the FUFF again and in a minute I found the /orders endpoint:
https://redacted.com/app/admin/orders
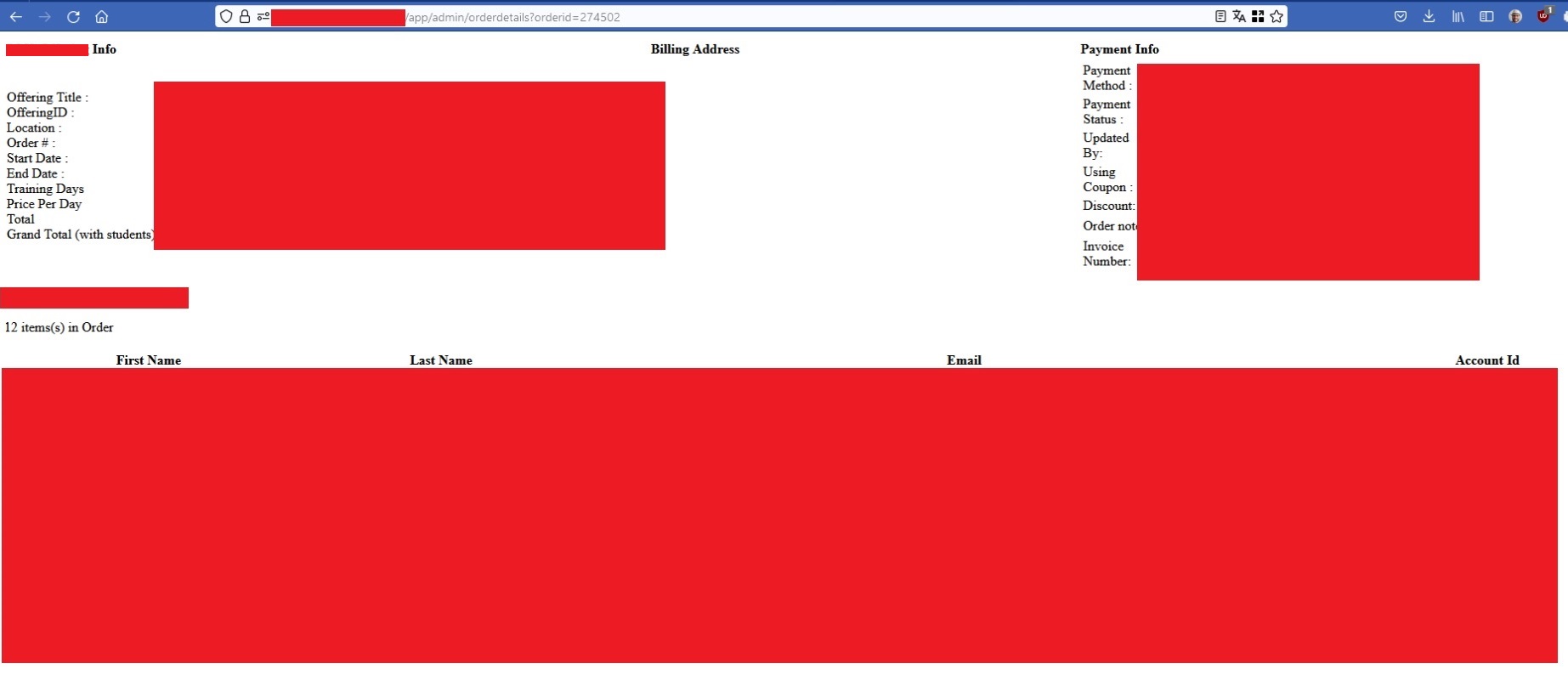
which returned a code with order IDs and numbers. Ok if we have some list of orders, now there must be an endpoint to view the order details. I tried to look for it somewhere in JavaScript files, with no luck, though. As I was already familiar with the app, I tried to guess it. After some trial and errors I guessed both endpoint and parameter name and it was:
https://redacted.com/app/admin/orderdetails?orderdid=1
I could view the details of the first order in the system.
Digging in js files
So far so good. I could report it, but if I found these two endpoints, there must be more of them. I tried to fuzz this admin endpoint some more with FUFF using different lists but with no luck :(. Next day with fresh mind I decided to dive into javascript files by hand. I clicked around the app , logging the requests in burp and then looking through the js files. After a while I found some big chunks of commented out js code. And there where some endpoints I’ve never seen before using that app. I thought that these might be some admin endpoints as they started with: delete, remove, publish, unpublish words. It was some kind of e-learning app, so let’s assume these endpoins were like:
https://redacted.com/app/admin/deleteCourse
https://redacted.com/app/admin/removeCourse
https://redacted.com/app/admin/unpublishCourse
https://redacted.com/app/admin/publishCourse
Reading js files and ajax requests I could easily construct the proper requests as I had the endpoints, the methods and the parameters.
The POC
The hard part was to create the POC not damaging any data in the app. As I could not create my own course, I decided to find the endpoint which gets the course id and then based on the responses, find the one that does not exist. That was pretty easy , just using the app and logging the requests. Then I used this course id in the endpoints mentioned above. If The status code returned 200, that was the proof the endpoints were not properly secured. After some digging I found some more enpoints. I reported all the finding and was rewarded a nice bounty.
Reward : 2000 USD
See you next bug
