Hi there
There was an app which allowed me to buy domains and offered different types of hosting. First I was testing the free features of the app and found really cool XSS bug but it is the different story :). Then I decided to invest some money and bought the domain, let’s call it mynewshinydomain.com, which costed me about 2 dollars. I took this financial risk 🙂
Once I bought it, I immediately gained access to tons of new features. And one of them was feature where I could upload or create files and dirs via web interface. I could only host static files such as .css, .html, .js, .txt, no scripts. But this isn’t important. There was also the option to upload the zip file, which later was extracted into the root of my site. As I am familiar with basic zip attacks such as zip-slip attack nad symlink attack, I tried both of them, but only the second one worked.
The zip symlink attack
In this attack we must zip the file which is symbolic link. The symbolic link is a kind of shortcut, it points to another file on file system. I created the test.txt file pointing to /etc/passwd on my system in WSL shell:
$ ln -s /etc/passwd test.txt
Then I zipped the file into test.zip
$ zip –symlinks test.zip test.txt
Note the –symlinks option to preserve the symlinks. I uploaded the file , I saw no errors, so I entered this url:
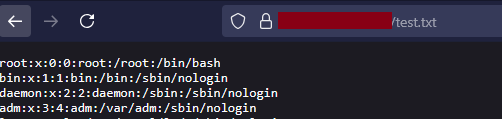
https://mynewshinydomain.com/test.txt
Wait, what? I could not believe I saw the content of /etc/passwd from the server. It worked just like this, no filters. So I obtained arbitrary file read, I could read files on server where web user has access to.
I immedietaly reported it as critical finding and after short time I got P1 and some cash :). They introduced the fix which I tried to bypass with binary editing of zip file but failed :/. My mistake was to report it right away, because I could maybe read some source code of an app and this way was able to find more vulns. On the other hand the attack is not complicated, so I was afraid of being duplicated and the emotions took over.
The final notes
- Sometimes it pays off to spend some money which gives access to more features to test.
- Let’s not assume anything upfront, even the pretty simple attacks might still work.
Impact: High
Reward: $750
See you next bug
